Timing attacks can be used to securely protect microcontrollers based on passwords, or to use a certain number of cards or passwords for access control systems, such as iButton products in Dallas. The common risk in these systems is that the consecutive numbers entered are checked again in the database.
First understand what MCU is-namely structure and composition
â… : Central processing unit CPU, including arithmetic unit, controller and register group. It is the core component inside the MCU, which consists of two parts: arithmetic component and control component. The former can complete data arithmetic and logic operations, bit variable processing and data transfer operations, while the latter coordinate work according to a certain time sequence and is a component that analyzes and executes instructions.
â…¡: Memory, including ROM and RAM. ROM program memory, the work of the MCU is executed one by one according to the pre-programmed program. The ROM program memory is used to store the programmed program (the system program is programmed and written by the manufacturer). The stored data does not disappear after power failure. ROM is divided into on-chip memory and off-chip (extended) memory.
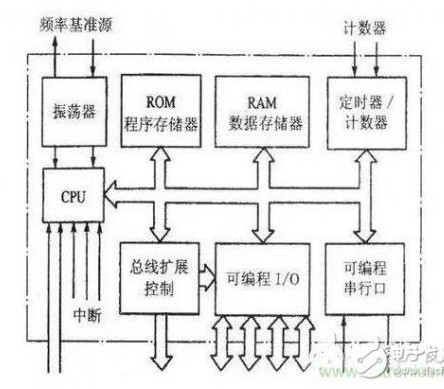
RAM data memory, data can be written at any time during the running of the program, and data can be read at any time. The stored data cannot be retained after power failure. RAM is also divided into on-chip data memory and off-chip (extended) memory.
â…¢: Input and output I/O interface, connected with external input and output (circuit) equipment. PO/P1/P2/P3 and other digital I/O interfaces, the internal circuit includes port latches, output drivers and input buffers. Among them, PO is a three-state bidirectional interface, P1/P2/P3 digital I/O port, the internal driver is an "open collector" output circuit, and the internal or external circuit is connected with a pull-up resistor during application. Each port can be used as a digital signal input or output port, and has multiplexing functions (referring to the port function has a first function, a second function or even several functions, which can be flexibly set in the application).
In addition to the digital I/O port, the MCU device also has ADC analog input and output ports. The input signal is converted into a digital (frequency) signal by the internal A/D conversion circuit, and then processed; for the output analog signal, then After D/A conversion, output to external circuit.
Let's talk about several methods of how to crack the MCU
1. Non-intrusive attacks
No need to initialize the components. When attacking, you can put the components in the test circuit for analysis, or you can connect the components separately. Once successful, this kind of attack is easy to spread, and re-attack does not require a lot of overhead. In addition, the use of this attack leaves no trace. Therefore, this is considered to be the biggest threat to the hardware security of any component. At the same time, it usually takes a lot of time and energy to find non-invasive methods of attacking specific components. This usually reverse-engineers the components, including disassembling software and understanding the hardware layout.
Non-intrusive attacks can be passive or active. Passive attack, also called side attack, does not have an effect on the components being attacked, but it is usually to observe its signals and electromagnetic radiation. Such as power analysis and clock attacks. Active attacks, such as brute force attacks and noise attacks, are characterized by adding signals to components, including power lines.
A simple non-intrusive attack can be to copy a power-on configuration of an SRAM-based FPGA. Connect the JATG interface used to configure the chip, and use an oscilloscope or logic analyzer to capture all signals. Then you can analyze the waveform and reply to unique commands.
When only half of the FPGA resources are used, the data flow can be slightly changed to disguise the fact of piracy. Leave a little space during configuration without affecting the operation of components. The JTAG interface also has some freedom when sending signal timing, so the pirated waveform can be set to look different from the original signal. In addition, the cracker can exchange row addresses when uploading, which gives the impression of a completely different design.
Vagueness and safety
Semiconductor manufacturers have provided major customers with measures to enhance the ability to prevent cracking of their products: customer printing on the packaging replaces the standard chip model. This gives the impression that the product is designed by a custom integrated circuit. As we all know, ASIC provides good protection measures to prevent a variety of attacks, and only a few experienced and well-equipped crackers can successfully crack. This will discourage many potential crackers. But a confident cracker will try to use simple methods to determine whether the chip is a real ASIC. The easiest way is to observe the pins connected to the power supply, ground, clock, reset, serial port or other interface. Compared with the suspected microcontrollers in the database, this result is very reliable, and each microcontroller has its own pin characteristics. Once found similar, put it on the universal programmer and try to read the result.
Another simple method is to restrict access to program memory. Usually used in smart cards, but also used in some microcontrollers. This is not a very reliable and practical method. Of course, it works well in smart cards, and all customers are forced to sign non-proliferation agreements with chip manufacturers. But microcontrollers rarely do this, and microcontrollers that can be programmed by universal programmers can be provided by many companies in the world. Even if there is no programming specification in the file, a low-cost oscilloscope can be used to generate the required waveform in a few hours. If the microcontroller is not supported by a special universal programmer, you can still obtain a direct and complete agreement by purchasing a development board from the manufacturer.
2. Timing attacks
Some security-related operations use input values ​​and keys, which are performed by the semiconductor chip at different times to compare. Careful timing measurement and analysis can recover the key. This method was first mentioned in the literature in 1996. Later this attack successfully cracked the actual RSA-signed smart card.
In order for the attack to succeed, it is necessary to collect device information and compare it with processing time, such as quesTIon-answer delay. Many cryptographic algorithms are vulnerable to timing attacks, and the main reason is that software executes the algorithms. That includes executing branches and operating conditions that are needed to skip in time; using caches; processing instructions such as frequency multiplication and frequency division at irregular times; and a large number of other reasons. The result is that execution capability typically depends on the key and input data.

To prevent such attacks, blind signatures (Blinding signatures) technology can be used. This method uses the selected random number to be mixed with the input data to prevent the cracker from knowing the mathematical algorithm of the input data.
Timing attacks can be used to securely protect microcontrollers based on passwords, or to use a certain number of cards or passwords for access control systems, such as iButton products in Dallas. The common risk in these systems is that the consecutive numbers entered are checked again in the database. The system needs to check every byte of the key input to the database frequently. Once an incorrect byte is found, it will stop immediately, and then switch to the next until the last one. Therefore, it is easy for a cracker to measure the time it takes to enter the last key before requesting another one, and get the similarity of the keys found. Try a relatively small number, it is possible to find a matching key.
To prevent these attacks, designers need to carefully calculate processor cycles. When comparing passwords, make sure that the correct and incorrect times are the same. For example, the internal memory load module of Freescale's 68HC08 microcontroller can access the internal flash memory after entering the correct eight-byte password. In order to achieve the same time for processing both correct and incorrect passwords, additional no-operation instructions have been added to the program. This provides good protection against timing attacks. Some microcontrollers have internal resistance-capacitance oscillators, so that the operating frequency of the processor is related to the voltage and the temperature of the chip. This makes time sequence analysis very difficult. It is necessary to stabilize the temperature of the components and reduce the noise and voltage fluctuations on the power line during the attack. Some smart cards have an internal random clock signal that invalidates the measurement time delay during an attack.
3. Brute force attacks (also called Brute force attacks)
Violence has another meaning for semiconductor hardware and cryptography. For passwords, a brute force attack is a large number of attempts on the system. Usually a high-speed computer is used to find a matching key. An example is the password protection setting in the microcontroller. Taking TI’s MSP430 as an example, the password itself is 32 bytes (256 bits) long, which is sufficient to resist brute force attacks. But the password is allocated at the same memory address as the processor interrupt vector. Then, first reduce the area that the vector always points to in the memory. Then when the software is updated, only a small part of the password is changed, because most of the interrupt subroutines point to the same address.
As a result, if the cracker knows one of the earlier passwords, it is easy to do a systematic search and find the correct password within a reasonable time. Brute force attacks can also be implemented in ASIC or CPLD hardware design. In this case, the cracker uses all possible logical combinations to the possible inputs of the components and observes all the outputs. This method is also called black-box analysis, because the cracker does not know the condition of the component under test. Through all possible signal combinations, try to get the function of the components. This method is effective for relatively small logic devices. Another problem is that the ASIC or CPLD used by the cracker has triggers, so the output may be the current state or the input state. But if the signal is checked and analyzed in advance, the search range can be significantly reduced. For example, clock input, data bus and some control signals are easy to recognize.
Another possible brute force attack, effective for many semiconductor chips, is to apply an external high voltage signal (usually twice the power supply voltage) to the chip pins to try to enter the factory test or programming mode. In fact, these pins are easy to find with a digital multimeter, because they do not have a protective diode to the power supply pin. Once a pin that is sensitive to high voltage is found, the cracker can try possible logic signal combinations to add to other pins to find the part that is used to enter the factory test or programming mode. The cracker can also use the communication protocol of the component to find out the hidden functions that the designer has embedded in the software for testing and updating.
Chip manufacturers often provide embedded hardware test interfaces for later testing. If the security protection of these interfaces is not properly designed, it is easy for a cracker to use it to read and write on-chip memory. In smart cards, these test interfaces are usually located outside the chip circuit and are physically removed after testing. Any security system, regardless of software and hardware, may be flawed in design, which is an opportunity for crackers, and brute force attacks may find it. Careful design of the security protection system and proper evaluation can avoid many problems and make these attacks practically infeasible.
Can be applied to all kinds of supermarkets, chain store POS ticket printing It can be used for catering, entertainment, automatic inquiry, automatic number picking and other bill printing Features: Adopt high-performance imported Thermal Printer core Simple and practical easy loading paper structure Optional Centronics parallel interface or RS-232 serial interface Speed up to 100mm/s Both parallel and serial interfaces Support nine kinds of barcode printing Support large print, center print Supports a variety of command systems and drivers
80Mm Thermal Printer,Thermal Inkjet Printer,Portable Thermal Printer,Thermal Sticker Printer
ShengXiaoBang(GZ) Material Union Technology Co.Ltd , http://www.sxbgz.com